 |
|
The following is a list of current or recent projects investigated by my research team. Selecting a project will provide more details about the work.
|
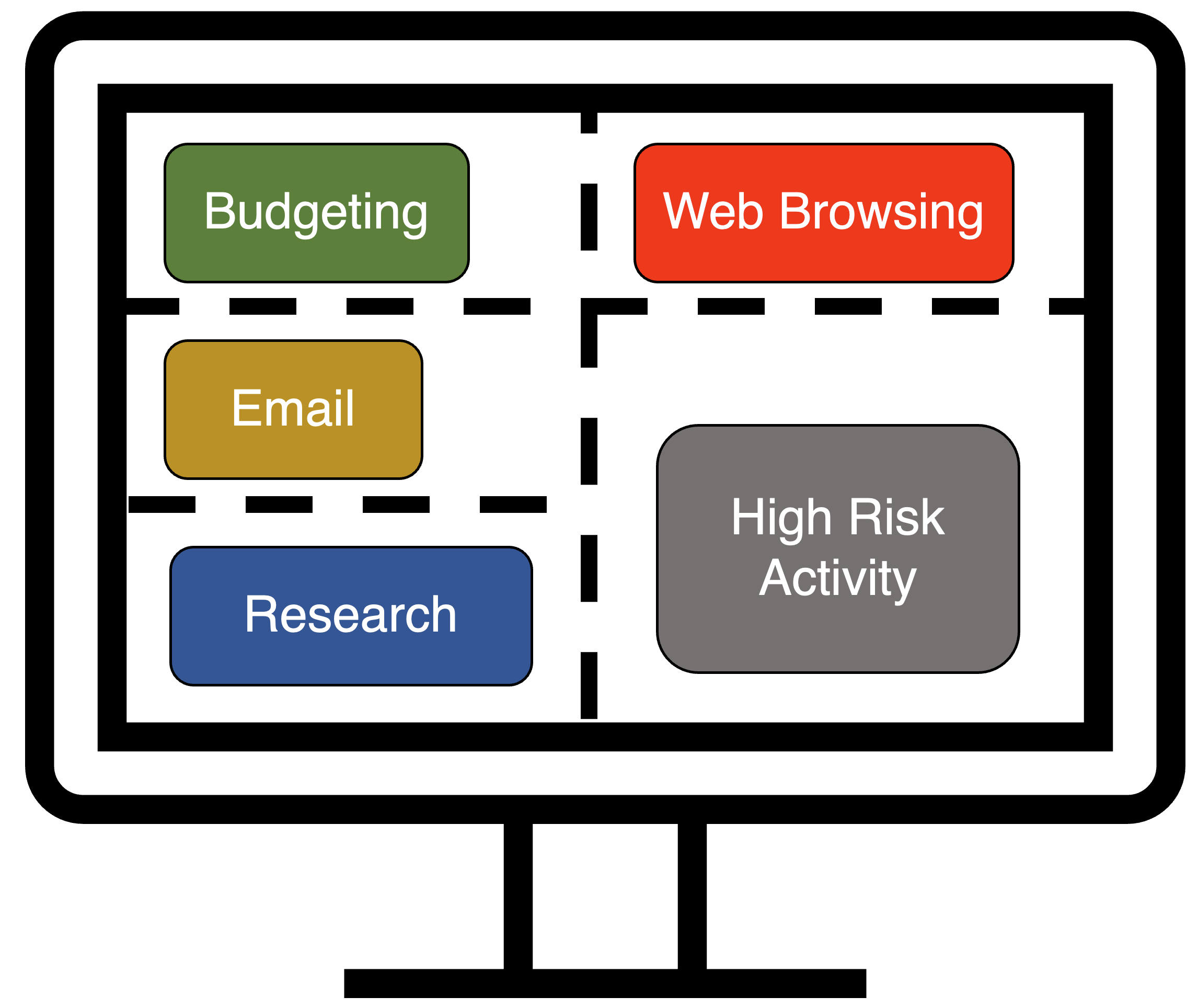
Some operating systems allow for fine-grained isolation of applications using virtualization. These tools are useful for ensuring security goals, but they can be difficult to configure and use. We are examining ways to combine organization computer fleet management tools, like JAMF, SCCM, and Puppet, with these operating systems to allow organization IT to help users create and use the right risk management domains. The goal is to give end-users the freedom to manage low-risk environments and configure software tools while ensuring security in high-risk environments with sensitive assets. Learn more at the project page. |
|
|
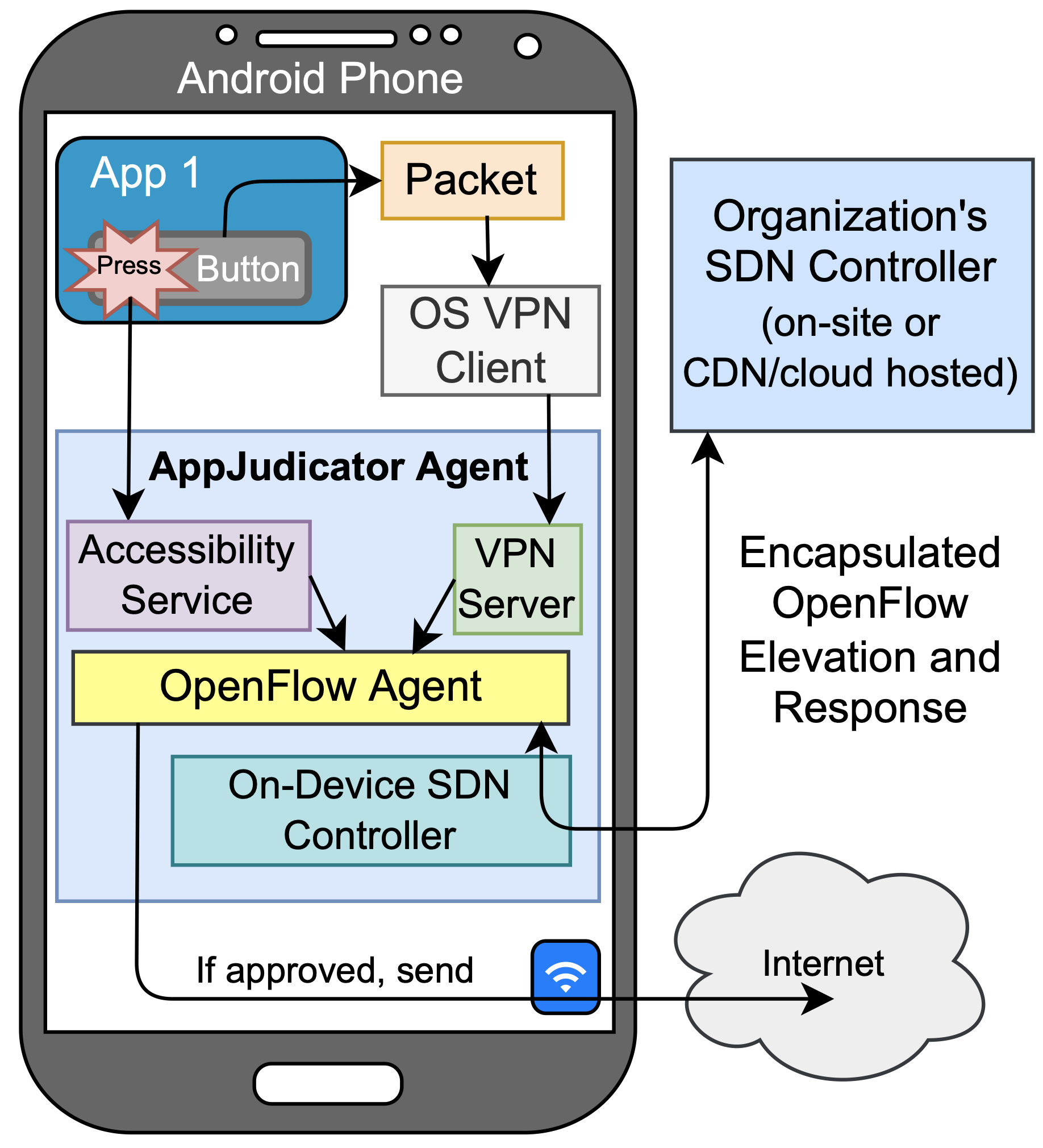
We explore ways to apply cutting-edge, enterprise-level software-defined networking technologies to mobile devices at a low cost and without requiring end-user expertise. We are examining ways to instrument the Android OS and user interface to allow detail network profiling that can distinguish user-driven activities from those associated with malware. Learn more at the project page. |
|
|
In our research, we seek to eliminate confused deputy attacks and the ability for a malicious client to affect others. We do so by eliminating the shared infrastructure associated with these public-facing servers. Rather than provide a single server that many clients use, we create a unique, single-use server for each client. While such an approach would be infeasible with physical infrastructure and prohibitively costly even with virtual machines, we can use lightweight containerization technology to isolate each instance of a public-facing server. When a client ends its session, we simply discard the container, eliminating the ability for an attacker to implant code that will affect future users. Finally, the single-use technique allows us to customize the permissions associated with each container, avoiding the need for highly-elevated privileges that enable the confused deputy attack. Learn more at the project page. |
|
|
To minimize risk to the OS and other accounts on a system, organizations often limit their users to the minimal privileges needed on the system. To limit threat propagation within the network, organizations use firewalls and virtual LANs (VLANs) to group hosts into smaller risk pools. They then use monitoring tools, such as intrusion-detection systems (IDS), at the network boundaries between groups to detect threats. Unfortunately, these enforcement and monitoring tools lack visibility into hosts and other parts of the network, hindering their ability to make informed decisions. Specifically, 1) they are blind to activity among grouped hosts (e.g., within VLANs or subnets), 2) they are blind to the host-level cause (or catalyst) of the network traffic when making security decisions, 3) they can only examine a subset of the network's traffic without seeing network-wide behavior, 4) they allow adversaries to perform reconnaissance on the organization's network and infrastructure, and 5) they use broad rules to allow or deny traffic without the ability to consider details. This work seeks to create centralized access control systems for all network traffic and to inform the network access controller of the host-level context and catalyst of network traffic. Learn more at the project page. |
|
|
While the software-defined networking (SDN) paradigm has had a significant impact on enterprise networks, in particular in data centers, it has not spread to residential users. But, the fundamental properties of SDNs, namely the outsourcing of management and control, are key enablers of a shift in how we manage residential networks. In our research, we have modified the TP-LINK TL-WR1043ND v2 wireless router with a custom OpenWRT firmware image that enables OpenFlow support. We then created an OpenFlow controller in the Amazon EC2 cloud and configured the router to elevate traffic to the cloud controller. In our research, we confirmed that the latency overheads inherent in the approach would be acceptable in practice. This research project will study the data collected from multiple residential routers to evaluate the feasibility of OpenFlow. The approach will also examine the feasibility of selectively proxying traffic through VMs in EC2 to enable IDS and protocol-aware firewalling techniques. Learn more at the project page. |
|
|
There are many deployed approaches for blocking unwanted traffic, either once it reaches the recipient's network, or closer to its point of origin. One of these schemes is based on the notion of traffic carrying capabilities that grant access to a network and/or end host. However, leveraging capabilities results in added complexity and additional steps in the communication process: Before communication starts a remote host must be vetted and given a capability to use in the subsequent communication. In this paper, we propose a lightweight mechanism that turns the answers provided by DNS name resolution - which Internet communication broadly depends on anyway - into capabilities. While not achieving an ideal capability system, we show the mechanism can be built from commodity technology and is therefore a pragmatic way to gain some of the key benefits of capabilities without requiring new infrastructure. Learn more at the project page. |
|
|
We have developed an approach that can quickly geolocate Internet users that are connected through a WiFi network. To do so, we send specially-crafted signals to the user's IP address. When these signals are broadcast by the user's wireless router to the user's wireless device, they have a discernible signature. We then use other geolocation efforts to scope the Internet user's location (e.g., to the appropriate city or section of a city). We then drive through the search area listening on wireless channels for the discernible wireless signature. Once we find it, we use directional antennas and triangulation to exactly locate the user. Learn more at the project page. |
|