 |
|
Attackers regularly compromise the public-facing servers that organizations use to fulfill their missions. We regularly change the locations of these servers, disorienting attackers, while still providing reliable connectivity for legitimate users.
Most organizations face on-going and damaging attacks on their public-facing servers. At the same time, such servers are critical to the mission objectives of these organizations. However, each server can became an attack vector and a foothold for adversaries into an organization's network. The cost of a security failure can be high. In 2011, the average cost of a data breach was estimated at $5.5 million. Other costs may be less quantifiable, including damage to the customer's reputation or even the customer's ability to complete its mission.
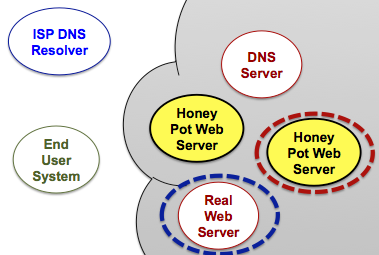
We frequently change the public addresses of protected servers, which 1) makes it challenging for attackers to guess the server's address and 2) allows us to seamlessly redirect an attacker to monitoring infrastructure (called a "Honey Pot").
When contacted by a legitimate user, the DNS server provides the correct address for the server and creates a network mapping to maintain the link.
This approach allows the DNS server to grant or deny access to users and seamlessly transition malicious users to honey pots upon detection. Organizations can use prior history to make decisions, protecting themselves based on past actions by a network.
The Choreographer project has been explored by the scientific community, resulting in two peer reviewed publications. The first, published in the ACM SIGCOMM Computer and Communication Review [ PDF ], describes the idea of a DNS capabilities system. The second, published in the ACM/IEEE Transactions on Internet Technology [ PDF ], describes how DNS resolvers can be profiled to determine whether access should be granted.