SSH public key and its distribution
In directory on SSH server /etc/ssh, there are multiple files which store public/private
key paris. We take ECDSA public key as an instance. (About key exchange negotiation you may need
to visit wiki). /etc/ssh/ssh_host_ecdsa_key file is the ECDSA private key. Corresponding
public key contained in /etc/ssh/ssh_host_ecdas_key.pub
Open ECDSA public key file on the same VM:
Remove the prefix 'ecdsa-sha2-nistp256' and suffix 'root@VM', the middle section is the real public key.
More specifically, it's the base64 encoded public key. You can also get this part by command
awk '{print $2}' ssh_host_ecdsa_key.pub.
Now let's examine how SSH public key is distributed, by server, to client.
According to this section from RFC4253:
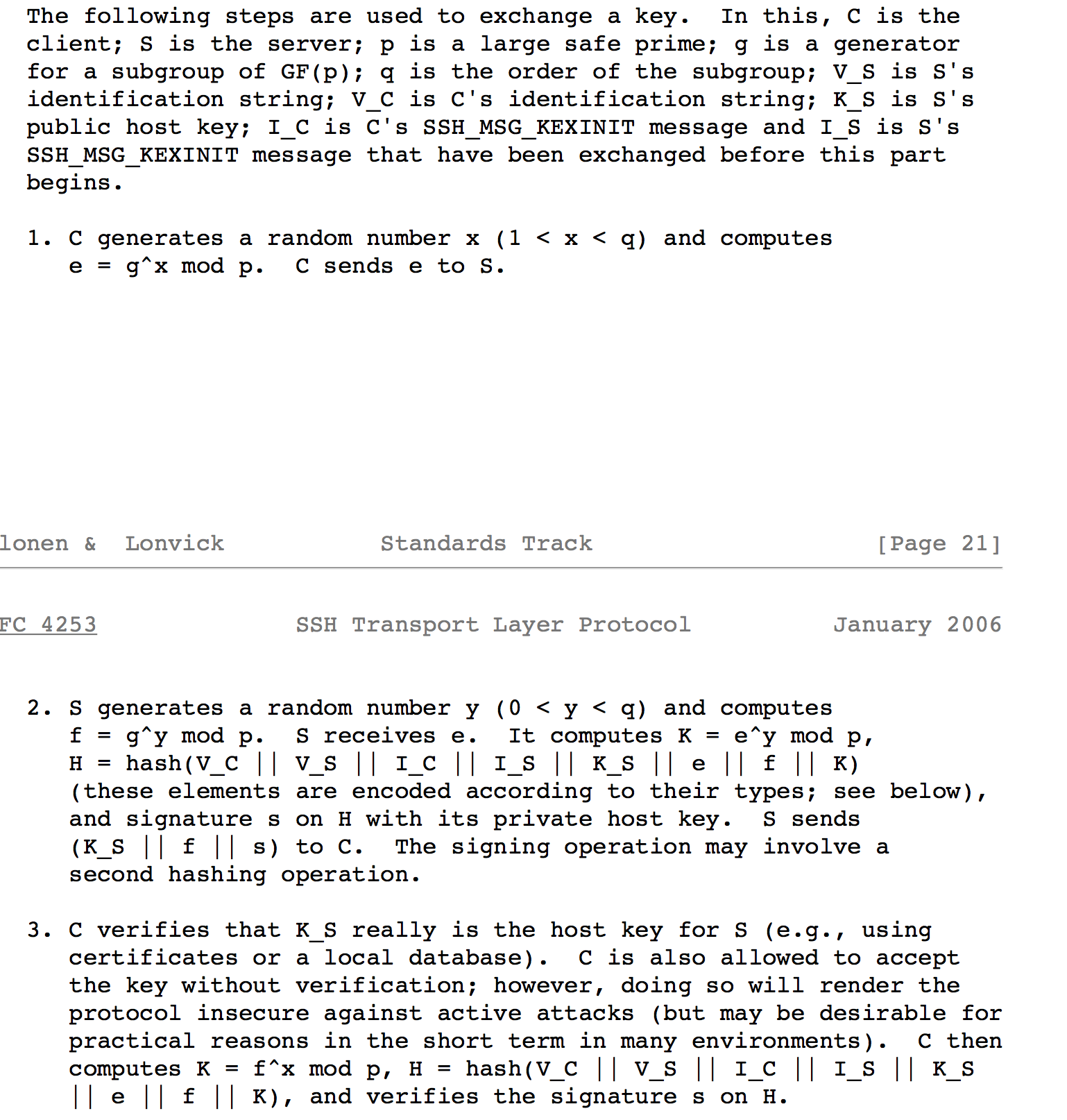
we can see the public key (K_S) should be sent from server to client as plaintext. That is to say, we should be able to find the public key from packets.
Now let's have a look at the packets.
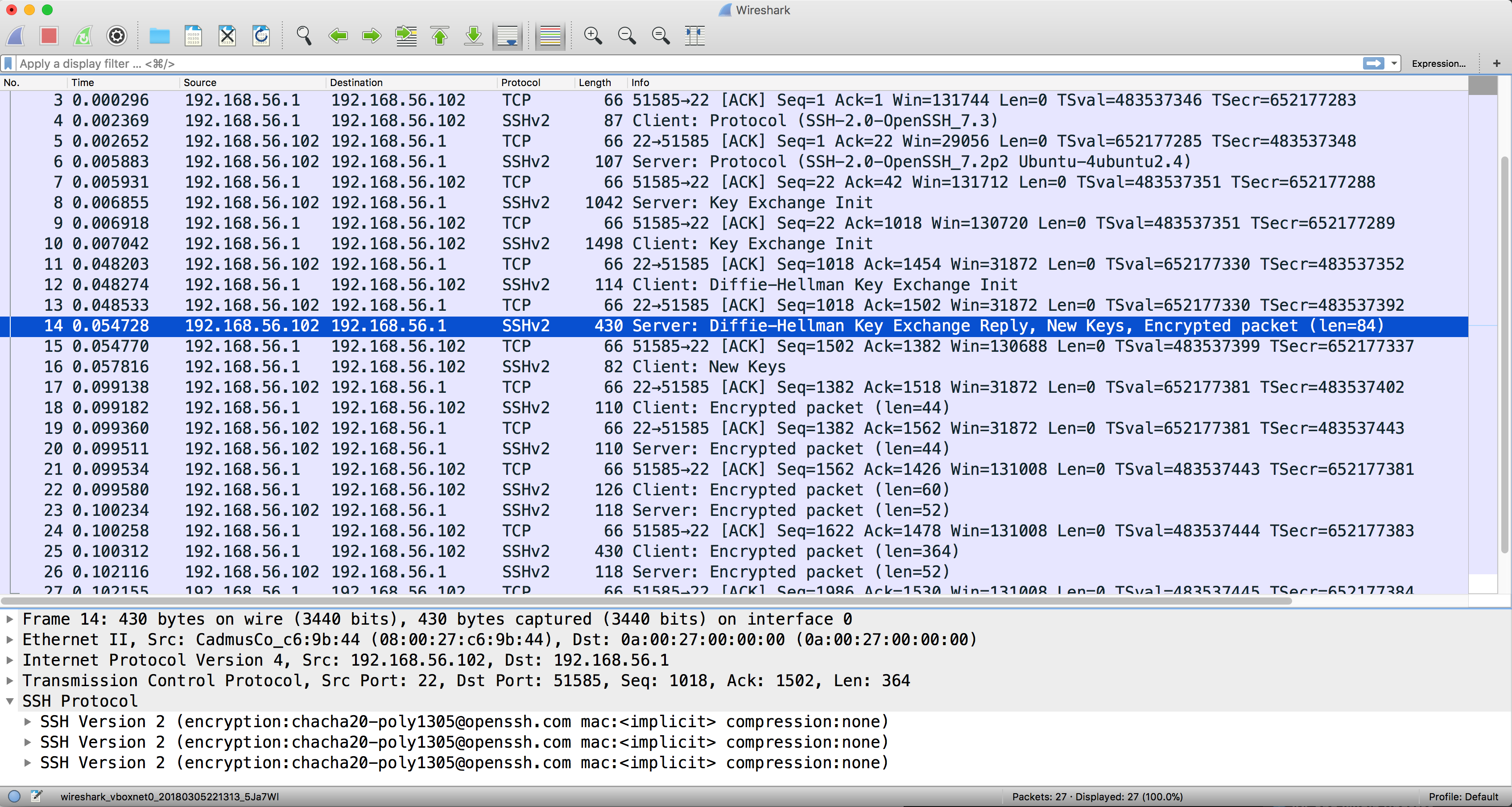
The key response is included in the 'key exchange reply' packet. Click on the packet, we have:
In the section of 'SSH Protocol', expand the first 'SSH Version 2' dropdown. (Others are not related, you should explore by your own if you are interested).
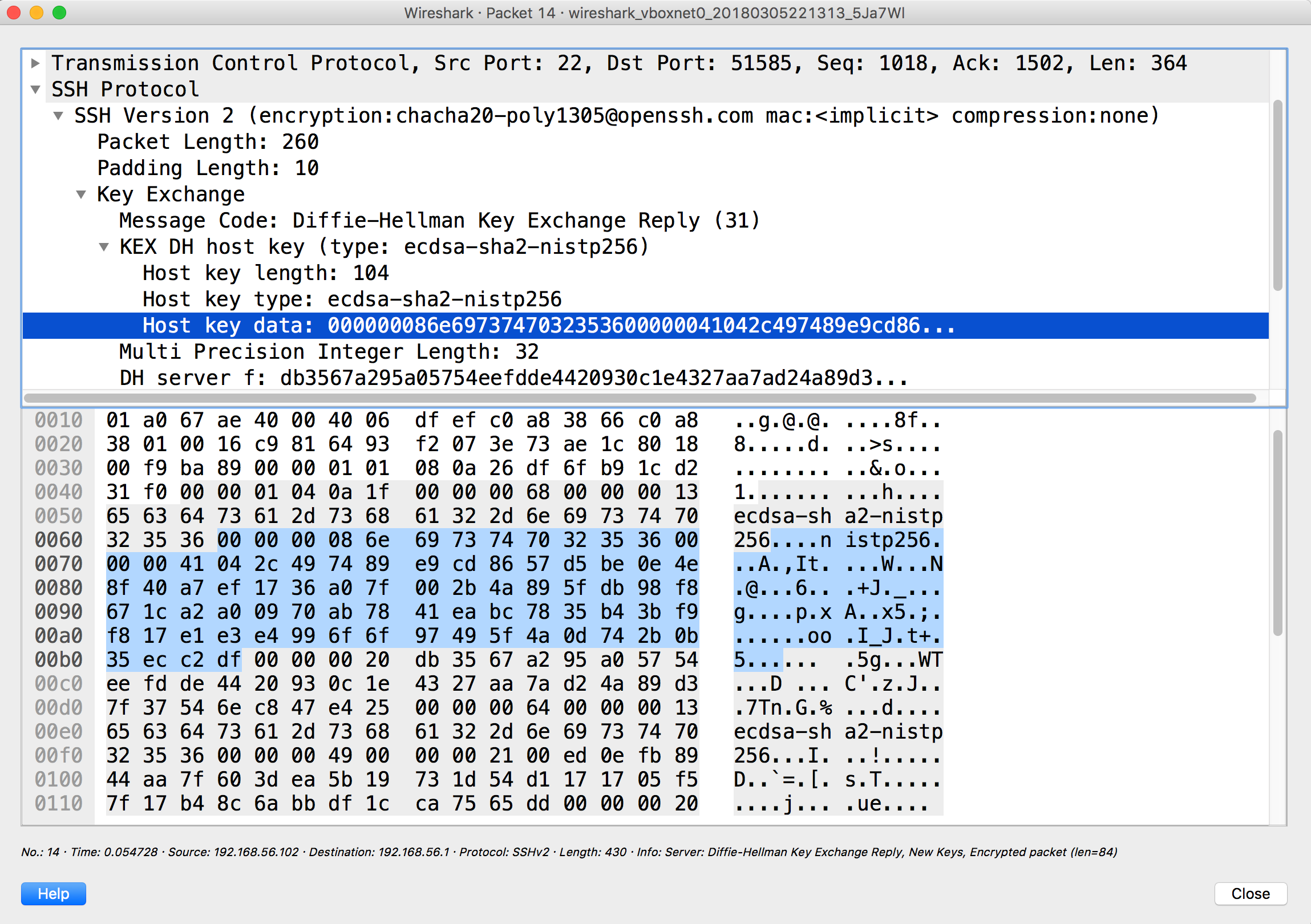
The highlighted part is the public key (not base64 encoded).
If you noticed all the bold words about base64 so far, you may raise assumption that if we do a base64 encoding on the highlighted section, the output should be same with the middle section of file 'ssh_host_ecdsa_key.pub' mentioned before.
Now run the command awk '{print $2}' ssh_host_ecdsa_key_pub | base64 -d to see what happens.
If you want to try the example case and verify your operation with mine case, you can just run echo AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCxJdInpzYZX1b4OTo9Ap+8XNqB/ACtKiV/bmPhnHKKgCXCreEHqvHg1tDv5+Bfh4+SZb2+XSV9KDXQrCzXswt8= | base64 -d
The output should be like:
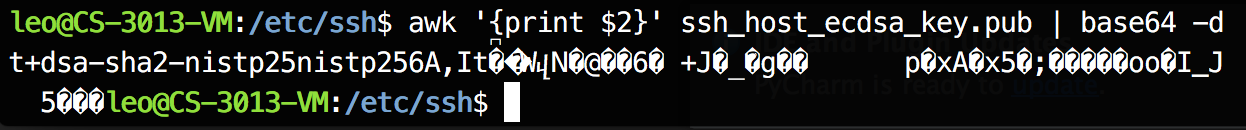
It's same with the highlighted section in the packet, right? Yes, this is how public key distributed.
Some explanation: public key is always stored in form of base64 on the server. One of the reason should be we want to present it as printable characters for display to users. (Base64 encoding replaces all the raw bytes to 64 readable characters. Details please head to wiki.) But we don't have to do this when transfering it to the other side through packets as non-expert users don't care what is on the wire. If you ask why not sending them also in form of base64, I don't know so far, that's how it works.
Then we should be able to recreate the encoded file by encoding the bytes with base64. It was a hard time to find the right input string from packet to be encoded and get exactly same output with the file, but it's provided:
0000001365636473612d736861322d6e69737470323536000000086e6973747032353600000041042c49
7489e9cd8657d5be0e4e8f40a7ef1736a07f002b4a895fdb98f8671ca2a00970ab7841eabc7835b43bf9
f817e1e3e4996f6f97495f4a0d742b0b35ecc2dfYou should be able to find the correct section if you need by comparing the example.
Conclusion: SSH public key is stored as base64 coding. It's distributed from server to client by bytes, which is from decoding the file '/etc/ssh_host_ecdsa_key.pub'